Here is a good offer for my readers.If anybody need rapidshare accounts,itunes giftcards,amazon giftcards etc for low price, contact sellser@yahoo.com.
You can get products at nearly half of original price..Enjoy the offer!!
ubuntu7.04
Wednesday, April 9, 2008
Sunday, November 4, 2007
BBC loses 97200 Linux users!
Every now and then The Register publishes a really funny news piece, and the one entitled 'Confused BBC tech chief' is a perfect example. According to the report, in an interview with UK based web design magazine .net, the Director of Future Media and Technology at the BBC, one Ashley Highfield, claimed that only 400 to 600 of the visitors to the BBC website were using Linux. That's 400 to 600 out of the 17.1 million users of the site.
"We have 17.1 million users of bbc.co.uk in the UK and, as far as our server logs can make out, 5 per cent of those [use Macs] and around 400 to 600 are Linux users" Highfield is quoted as saying.
Although it is easy to understand that actual numbers are never going to be possible to reap from server logs, especially when the browser user agent string can so easily be adjusted by users of Linux for example, it is still useful as a trend reporting device. Indeed, according to the CurryBetDotNet, the blog of a former BBC new media employee, if you go back a couple of years the BBC were saying then that Linux represented a 0.41 percent visitor share which would be over 70,000 rather than 600 max.
So what has Highfield got to say by way of an explanation?
Responding to the criticism of the figures in the BBC blog, Highfield comments "Alternative analysis that we have run off which performs the measurement in different ways suggests that the potential number of Linux users could range from 0.3% to 0.8% (which, from a total UK bbc.co.uk userbase of 12.2m weekly users could imply a user base between 36,600 and 97,600.) We'll try and get a more accurate picture: over 30 thousand Linux users is a not insubstantial number, but we do have to keep this in context with the vast majority of users who use either Windows or Macs to access bbc.co.uk."
Not that Highfield is a stranger to controversy when it comes to Linux by the numbers.
Take the small matter of the iPlayer, the BBC's move into streamed TV broadcasting content, which has been hit by claims it is ignoring Linux users. In that same .net magazine, Highfield responded to claims that open source protestors had been gathering outside the BBC's HQ in London as a result of the Windows only iPlayer by saying "The 12 people who demonstrated outside our offices have every right to demonstrate, but I think 'the 12 people' says it all."
"We have 17.1 million users of bbc.co.uk in the UK and, as far as our server logs can make out, 5 per cent of those [use Macs] and around 400 to 600 are Linux users" Highfield is quoted as saying.
Although it is easy to understand that actual numbers are never going to be possible to reap from server logs, especially when the browser user agent string can so easily be adjusted by users of Linux for example, it is still useful as a trend reporting device. Indeed, according to the CurryBetDotNet, the blog of a former BBC new media employee, if you go back a couple of years the BBC were saying then that Linux represented a 0.41 percent visitor share which would be over 70,000 rather than 600 max.
So what has Highfield got to say by way of an explanation?
Responding to the criticism of the figures in the BBC blog, Highfield comments "Alternative analysis that we have run off which performs the measurement in different ways suggests that the potential number of Linux users could range from 0.3% to 0.8% (which, from a total UK bbc.co.uk userbase of 12.2m weekly users could imply a user base between 36,600 and 97,600.) We'll try and get a more accurate picture: over 30 thousand Linux users is a not insubstantial number, but we do have to keep this in context with the vast majority of users who use either Windows or Macs to access bbc.co.uk."
Not that Highfield is a stranger to controversy when it comes to Linux by the numbers.
Take the small matter of the iPlayer, the BBC's move into streamed TV broadcasting content, which has been hit by claims it is ignoring Linux users. In that same .net magazine, Highfield responded to claims that open source protestors had been gathering outside the BBC's HQ in London as a result of the Windows only iPlayer by saying "The 12 people who demonstrated outside our offices have every right to demonstrate, but I think 'the 12 people' says it all."
Sunday, October 28, 2007
Amazing 3D view of linux kernels..
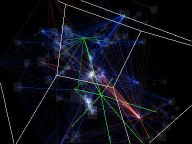
linux-1.2.0

linux-2.4.1
A guided tour of Linux-2.4.5: 9 MB MPEG (384x288, 2000 frames).
From 1.2.0 to 2.4.1: 12 MB MPEG (384x288, 1400 frames).
From 1.2.0 to 2.4.1: 4 MB MPEG (320x240, 1200 frames, low motion).
These are 3D renderings of dependencies in the Linux kernel source code.
Grey boxes are files.
The green tree is the directory structure. The two main hubs are "fs" and "net". The "drivers" tree is not rendered.
Blue lines are function dependencies.
Red lines are variable dependencies.
Yellow flashes show file size modifications.
Green flashes show files being moved across directories.
Red flashes show new files.
How this is done
For each kernel source tree, C files are preprocessed and parsed. Functions and static variables are cross-referenced. The resulting data structures (about 1MB each) are written to disk before rendering.
This takes up to 15 minutes for a recent kernel.
Some C files are excluded manually:
files which do not belong in the kernel (gentbl.c, skeleton.c, scripts, tools, ...)
arch/alpha, ... (only i386)
architecture-dependent drivers
C files which are #include'd (mmap_avl.c, ...).
Layout is done with trivial spring-based techniques. Links are weighted according to how often functions are used. This is why kernel/printk.c, kernel/sched.c etc get placed outside the core.
Color effects are computed by diff'ing successive versions.
The custom 3D renderer uses transparency effects rather than polygons and textures. It runs at interactive frame rates on small kernels.
Limitations
Timing currently reflects version numbers, not release dates.
Some structure information (e.g. macros) is lost through preprocessing.
Dependencies in __asm__ arguments are ignored.
Preprocessing errors and warnings are ignored.
CFLAGS in local Makefiles are ignored.
Some files in old kernels used to include headers from /usr/include (e.g. stdio.h). They are not processed correctly.
Some drivers won't compile without a proper combination of CONFIG_ #defines. They are not processed correctly.
The parser might be buggy because of unconventional side-effects and remaining reduce/reduce conflicts (i.e. I haven't tested it for any other application).
Interesting facts
There are files with CR/LF carriage returns in some old kernels.
Parsing C is fun. The following code demonstrates exciting features of GNU C used in old versions of Linux:
int a, b;
typedef int t, u;
void f1() { a * b; }
void f2() { t * u; }
void f3() { t * b; }
void f4() { int t; t * b; }
void f5(t u, unsigned t) {
switch ( t ) {
case 0: if ( u )
default: return;
}
}
source
The State of the Linux Gaming Industry
When I read reports on the Linux gaming industry, I can't help but wonder where the Linux gamers are at? Can we find them on the Nintendo Wii or perhaps the Playstation 3 (PS3)? After all, I have heard that PS3 actually works rather well with Yellow Dog Linux.
Now, I fear that if we plan to see the level of acceptance we are seeing with Ubuntu, the Linux gaming industry is going to have to make some tough choices. This will involve the licensing game developers choose, goals and profit models for those who remain open source, and of course, competing with the mega-giants like EA, who is happily working with Apple on the OS X platform .
Enter Loki: The One Best Hope At Porting Popular Windows Games to Linux. Even when considering the number of popular titles in Windows, it was nice to know that we had Loki pulling for the Linux users just a few years ago. Today, they are out of business due to bankruptcy. The remaining players in the non-open source Linux gaming world include " id " ( for now anyway ), Epic Games and others.
Some will argue that this is what these companies get for daring to bring forth a non-open source product to the Linux landscape. Personally, I find this attitude to be elitist and unfortunate as these games were not running on the slow moving mess laughingly called Cedega . No, they ran natively, and many of them ran quite well.
To be fair, it has been over a year since I've tried Cedega on a variety of different distros, but when Cross Over Office is providing me with better results than this option designed for gaming, something is seriously wrong. However, latest reports suggest that things are improving with Cadega.
A Fantastic Game for the Open Source At Heart. If you are tired of playing games like SuperTux and are ready to step up to something with 3D acceleration, great graphics and a gaming engine that offers everything you could want from a first person shooter, look no further. The 'Cube' gaming engine is the first thing to come out of the open source community that actually shows enough detail, a big enough fan base and interest in further development that it could quickly become a cult classic.
Offspring from the Cube Gaming Engine. Already, the Cube engine has generated enough interest to where three popular 'mods' (modifications from the original Cube) have taken shape.
Cube 2: Sauerbraten : This mod is a little less about glamor in gaming and more about a trip back to old-school gaming.
Cube 2: Eisenstern : To some limited degree, I see this as evolving into something even more than a basic single player game. With a little time, money and know-how, we might one day see this evolving into a World of Warcraft type clone. This would likely happen with another mod, though.
AssultCube : Perhaps the mod that will gain the most attention for gamers in the Linux world looking for the most realism in their first person shooter title. AssultCube is a very clean, well designed mod of Cube.
Finding Games, Open Source And Closed. For the uninitiated, locating great games to enjoy in Linux can be a bit troubling. I used to buy mine from Loki. Today, we continue to see two great resources that have weathered the pressures of the Windows gaming industry.
The Linux Game Tome : An old but valued resource that has stood the test of time. Despite the lack of clear gaming categories, this remains the king of gaming sources in my world.
Liberated Games : A resource that provides games for multiple platforms, some of which may already appear on the 'Tome' above. Liberated Games is still a good place to check out to see if anything has been released that is worth checking out.
All in all, the state of the Linux gaming industry is improving substantially, but it will take sometime before gaming giants, such as EA, focus on Linux and take it seriously as a platform. In the meantime, just like with everything in Linux, it's up to the community to band together and show enough demand for the heavyweights, or at least open source developers, to take notice.
Now, I fear that if we plan to see the level of acceptance we are seeing with Ubuntu, the Linux gaming industry is going to have to make some tough choices. This will involve the licensing game developers choose, goals and profit models for those who remain open source, and of course, competing with the mega-giants like EA, who is happily working with Apple on the OS X platform .
Enter Loki: The One Best Hope At Porting Popular Windows Games to Linux. Even when considering the number of popular titles in Windows, it was nice to know that we had Loki pulling for the Linux users just a few years ago. Today, they are out of business due to bankruptcy. The remaining players in the non-open source Linux gaming world include " id " ( for now anyway ), Epic Games and others.
Some will argue that this is what these companies get for daring to bring forth a non-open source product to the Linux landscape. Personally, I find this attitude to be elitist and unfortunate as these games were not running on the slow moving mess laughingly called Cedega . No, they ran natively, and many of them ran quite well.
To be fair, it has been over a year since I've tried Cedega on a variety of different distros, but when Cross Over Office is providing me with better results than this option designed for gaming, something is seriously wrong. However, latest reports suggest that things are improving with Cadega.
A Fantastic Game for the Open Source At Heart. If you are tired of playing games like SuperTux and are ready to step up to something with 3D acceleration, great graphics and a gaming engine that offers everything you could want from a first person shooter, look no further. The 'Cube' gaming engine is the first thing to come out of the open source community that actually shows enough detail, a big enough fan base and interest in further development that it could quickly become a cult classic.
Offspring from the Cube Gaming Engine. Already, the Cube engine has generated enough interest to where three popular 'mods' (modifications from the original Cube) have taken shape.
Cube 2: Sauerbraten : This mod is a little less about glamor in gaming and more about a trip back to old-school gaming.
Cube 2: Eisenstern : To some limited degree, I see this as evolving into something even more than a basic single player game. With a little time, money and know-how, we might one day see this evolving into a World of Warcraft type clone. This would likely happen with another mod, though.
AssultCube : Perhaps the mod that will gain the most attention for gamers in the Linux world looking for the most realism in their first person shooter title. AssultCube is a very clean, well designed mod of Cube.
Finding Games, Open Source And Closed. For the uninitiated, locating great games to enjoy in Linux can be a bit troubling. I used to buy mine from Loki. Today, we continue to see two great resources that have weathered the pressures of the Windows gaming industry.
The Linux Game Tome : An old but valued resource that has stood the test of time. Despite the lack of clear gaming categories, this remains the king of gaming sources in my world.
Liberated Games : A resource that provides games for multiple platforms, some of which may already appear on the 'Tome' above. Liberated Games is still a good place to check out to see if anything has been released that is worth checking out.
All in all, the state of the Linux gaming industry is improving substantially, but it will take sometime before gaming giants, such as EA, focus on Linux and take it seriously as a platform. In the meantime, just like with everything in Linux, it's up to the community to band together and show enough demand for the heavyweights, or at least open source developers, to take notice.
Wednesday, October 24, 2007
FreeBSD 7.0-BETA1 Available
FreeBSD® is an advanced operating system for x86 compatible (including Pentium® and Athlon™), amd64 compatible (including Opteron™, Athlon™64, and EM64T), UltraSPARC®, IA-64, PC-98 and ARM architectures. It is derived from BSD, the version of UNIX® developed at the University of California, Berkeley. It is developed and maintained by a large team of individuals. Additional platforms are in various stages of development.
Download AMD64 version
Download AMD64 version
Saturday, October 20, 2007
Top 10 Colleges for Gaming
The folks at Global Gaming League have compiled a very impressive list of the top 10 colleges that excel at gaming. They actually did a survey of students at many universities, so this is a real and factual list. We’re not talking about universities that teach gaming, rather ones with strong gaming culture among students with gaming clubs, frequent LAN tournaments, a fast campus Internet connection and other factors that embrace such tech trends.
But a growing number of students are choosing colleges based on their compatibility with video gaming. Super hi-speed connections and dedicated servers, big-screen TVs in lounges, gaming-related classes, social events centering around LAN parties and perks like free download licensing are increasingly part of the lure of certain schools.
That video gaming is now a consideration should not be surprising. These students grew up on video games and grew accustomed to a large part of their entertainment being delivered by multiplayer games instead of television, movies, books or other media They are an elusive, fickle and important demographic in today’s advertising markets, and choosey gamers are now an established subculture on U.S. campuses.
You can read the full list of details at GGL but here are the top 10.
1.University of Texas - Austin, Texas
2.Penn State University - State College, Pennsylvania
3.Rochester Institute of Technology - Rochester, New York
4.University of California at Los Angeles - Los Angeles, California
5.Digipen Institute of Technology - Redmond, Washington
6.University of Southern California, Los Angeles, California
7.Georgia Institute Of Technology - Atlanta, Georgia
8.University of Minnesota, Twin Cities campus - Minneapolis, Minnesota
9.University of Michigan, Dearborn Campus - Dearborn, Michigan
10.Full Sail Real World Education - Orlando, Florida
It’s no surprise that UT at Austin is on the list. Many of my friends from Houston attend UT and I know first hand what the gamer community is like there. With over 50,000 students, it’s impossible to avoid having a strong gaming environment. I was also pleased with the fact that Georgia Tech made it on the list. At the beginning of every year they hold a LAN party in the library for the freshmen. Many students at Georgia Tech are gamers as well, even the frat guys and sports jocks.
If that wasn’t enough to convince you that Tech is a top ten gaming school, consider its blazing Internet connection. Tech’s connection is so good that another local university piggybacks off its backbone. The reality is that the only thing keeping Tech out of the top five is its poor geographical location. The Atlanta gaming scene is fairly barren.
As far as a design curriculum, Tech has signed on as part of Microsoft’s new XNA development scheme, a new set of tools provided by the software giant to facilitate game design for its console and PC platforms. Tech will begin incorporating some of the development tools for the Xbox 360 into its classes this fall, but it did not have a very well-established game development program prior to this year.
But a growing number of students are choosing colleges based on their compatibility with video gaming. Super hi-speed connections and dedicated servers, big-screen TVs in lounges, gaming-related classes, social events centering around LAN parties and perks like free download licensing are increasingly part of the lure of certain schools.
That video gaming is now a consideration should not be surprising. These students grew up on video games and grew accustomed to a large part of their entertainment being delivered by multiplayer games instead of television, movies, books or other media They are an elusive, fickle and important demographic in today’s advertising markets, and choosey gamers are now an established subculture on U.S. campuses.
You can read the full list of details at GGL but here are the top 10.
1.University of Texas - Austin, Texas
2.Penn State University - State College, Pennsylvania
3.Rochester Institute of Technology - Rochester, New York
4.University of California at Los Angeles - Los Angeles, California
5.Digipen Institute of Technology - Redmond, Washington
6.University of Southern California, Los Angeles, California
7.Georgia Institute Of Technology - Atlanta, Georgia
8.University of Minnesota, Twin Cities campus - Minneapolis, Minnesota
9.University of Michigan, Dearborn Campus - Dearborn, Michigan
10.Full Sail Real World Education - Orlando, Florida
It’s no surprise that UT at Austin is on the list. Many of my friends from Houston attend UT and I know first hand what the gamer community is like there. With over 50,000 students, it’s impossible to avoid having a strong gaming environment. I was also pleased with the fact that Georgia Tech made it on the list. At the beginning of every year they hold a LAN party in the library for the freshmen. Many students at Georgia Tech are gamers as well, even the frat guys and sports jocks.
If that wasn’t enough to convince you that Tech is a top ten gaming school, consider its blazing Internet connection. Tech’s connection is so good that another local university piggybacks off its backbone. The reality is that the only thing keeping Tech out of the top five is its poor geographical location. The Atlanta gaming scene is fairly barren.
As far as a design curriculum, Tech has signed on as part of Microsoft’s new XNA development scheme, a new set of tools provided by the software giant to facilitate game design for its console and PC platforms. Tech will begin incorporating some of the development tools for the Xbox 360 into its classes this fall, but it did not have a very well-established game development program prior to this year.
Wednesday, October 17, 2007
Seven steps to increase Linux security
Ask a network administrator in any large organisation to compare Linux with network operating systems like Windows NT or Novell Open Enterprise Server, and chances are he'll admit that Linux is an inherently more stable and scalable solution. Chances are he'll also admit that when it comes to securing the system from outside attack, Linux is possibly the most difficult of the three to work with.
This perception is not an uncommon one -- many network administrators new to Linux find it hard to transition from a point-and-click security configuration interface to one based on editing complicated and hard-to-locate text files. Most administrators are well aware of the need to manually put in roadblocks and obstacles to trip up would-be hackers and ensure that your company's data stays secure; it's just that in the unfamiliar Linux world, they're not completely sure of their bearings or where to start.
That's where this document comes in. It outlines some easy things administrators can do to make their Linux server more secure and significantly reduce the risk they face. This tutorial lists seven such items.
1. Protect the root account
The root, or superuser, account on a Linux system is like a backstage pass at a Stones concert -- it allows you access to anything and everything. For this reason, it's well worth taking extra steps to protect it. Start by setting a hard-to-guess password for this account with the passwd command, change it on a regular basis, and restrict knowledge of the password to a few (ideally, only two) key people in the organisation.
Next, restrict the terminals that can be used for root access, by editing the file /etc/securetty. To avoid users leaving a root terminal "open", set a timeout for inactive root logins by setting the TMOUT local variable, and ensure that the root command history file (which might contain sensitive information) is disabled by setting the HISTFILESIZE local variable to 0. Finally, enforce a policy of using this account only to perform specific administrative tasks, and discourage users from logging in as root by default.
Tip: Once you've closed these holes, the next step is to require that every normal user account must have a password and ensure that passwords do not use easily-recognisable heuristics such as birthdays, user names or dictionary words.
2. Install a firewall
A firewall lets you filter data packets travelling in and out of your server and ensures that only those packets matching pre-defined rules are permitted to enter or exit. A number of excellent firewalls are available for Linux, and firewall code can even be compiled directly into the kernel. Begin by defining input, output and forwarding rules for packets leaving and entering your network, using the ipchains or iptables commands. Rules may be specified on the basis of IP addresses, network interfaces, ports, protocols or combinations of these attributes; these rules also specify what action (accept, reject, forward) to take when a match occurs. Once the rules are installed, test the firewall extensively to ensure that no holes exist in it. A good firewall is your first line of defence against common attacks like the distributed denial of service (DDoS) attack.
3. Use OpenSSH for network transactions
An important issue in client-server architecture involves the security of data being transmitted over the network. If network transactions take place in plaintext, it is possible for a hacker to "sniff" the data packets being transmitted and thus gain access to sensitive information. You can close this hole by using a secure shell utility like OpenSSH to create a secure encrypted "tunnel" for your data to pass through. Encrypting your connections in this manner makes it extremely hard for unauthorised users to read the data going back and forth between network hosts.
4. Disable unwanted services
Most Linux systems are installed with a wide variety of different services enabled, such as FTP, telnet, UUCP, ntalk and so on. In most cases, these services are rarely used and leaving them active is like leaving your windows open for a burglar to slip in. You can disable these services by commenting them out in the /etc/inetd.conf or /etc/xinetd.conf files and then restarting the inetd or xinetd daemon. Additionally, some services (for example, database servers) may start up by default during the boot process; you can disable these by editing the /etc/rc.d/* directory hierarchy. Many experienced administrators disable all system services, only leaving SSH communication ports open.
5. Use a spam and anti-virus filter
Junk e-mail and viruses annoy your users and can sometimes cause critical network failures. Linux is surprisingly resistant to viruses, but client machines running Windows may be more susceptible. Therefore, it's a good idea to install a spam and virus filter on your mail server itself, to "defang" suspicious messages and reduce the risk of a chain of collapses.
Begin by installing SpamAssassin, a leading open-source tool that uses a combination of different techniques to identify and flag spam; the program also supports user-based whitelisting and graylisting for greater accuracy. Next, install procmail for user-level filtering based on regular expressions; this tool allows automatic filtering of received email into mailboxes, at both a user and system level. Finally, install Clam Anti-Virus, a free anti-virus toolkit that integrates with sendmail and SpamAssassin and supports on-access scanning of email attachments.
6. Install an intrusion detection system
Intrusion detection systems (IDS) are early warning systems that let you know if changes occur on your network. They're a great way to identify (and prove) attempts to break into your system, although at the cost of increased resource consumption and potential red herrings. There are two fairly well-known IDS' you can try: tripwire, which tracks file signatures to detect modifications; and snort, which use rules-based directives to perform real-time packet analysis and search and identify attempts to probe or attack your system. Both packets can generate e-mail alerts (among other actions) and are useful when you suspect your network is being compromised but need definitive proof.
7. Perform regular security audits
When it comes to securing your network, this final step is possibly the most important. Here, you put on a black hat and do your best to circumvent the defences you erected in the previous steps. Doing this provides you with an immediate and objective assessment of how hard your system really is, and identifies potential vulnerabilities that you should fix.
A number of tools are available to help you in this audit: you can attempt to hack your password files using password crackers like Crack and John the Ripper; you can use nmap or netstat to look for open ports; you can sniff the network using tcpdump; and you can try exploiting publicised holes in your installed programs (Web server, firewall, Samba) to see if they offer a way in. If you do manage to find a way past your obstacles, rest assured that others will too; take immediate measures to close the openings.
Protecting your Linux system is an ongoing task, and so you shouldn't rest easy once you've done the steps above. Visit the Linux security forums for more security tips, and be proactive in monitoring and updating the security of your system. Good luck!
This perception is not an uncommon one -- many network administrators new to Linux find it hard to transition from a point-and-click security configuration interface to one based on editing complicated and hard-to-locate text files. Most administrators are well aware of the need to manually put in roadblocks and obstacles to trip up would-be hackers and ensure that your company's data stays secure; it's just that in the unfamiliar Linux world, they're not completely sure of their bearings or where to start.
That's where this document comes in. It outlines some easy things administrators can do to make their Linux server more secure and significantly reduce the risk they face. This tutorial lists seven such items.
1. Protect the root account
The root, or superuser, account on a Linux system is like a backstage pass at a Stones concert -- it allows you access to anything and everything. For this reason, it's well worth taking extra steps to protect it. Start by setting a hard-to-guess password for this account with the passwd command, change it on a regular basis, and restrict knowledge of the password to a few (ideally, only two) key people in the organisation.
Next, restrict the terminals that can be used for root access, by editing the file /etc/securetty. To avoid users leaving a root terminal "open", set a timeout for inactive root logins by setting the TMOUT local variable, and ensure that the root command history file (which might contain sensitive information) is disabled by setting the HISTFILESIZE local variable to 0. Finally, enforce a policy of using this account only to perform specific administrative tasks, and discourage users from logging in as root by default.
Tip: Once you've closed these holes, the next step is to require that every normal user account must have a password and ensure that passwords do not use easily-recognisable heuristics such as birthdays, user names or dictionary words.
2. Install a firewall
A firewall lets you filter data packets travelling in and out of your server and ensures that only those packets matching pre-defined rules are permitted to enter or exit. A number of excellent firewalls are available for Linux, and firewall code can even be compiled directly into the kernel. Begin by defining input, output and forwarding rules for packets leaving and entering your network, using the ipchains or iptables commands. Rules may be specified on the basis of IP addresses, network interfaces, ports, protocols or combinations of these attributes; these rules also specify what action (accept, reject, forward) to take when a match occurs. Once the rules are installed, test the firewall extensively to ensure that no holes exist in it. A good firewall is your first line of defence against common attacks like the distributed denial of service (DDoS) attack.
3. Use OpenSSH for network transactions
An important issue in client-server architecture involves the security of data being transmitted over the network. If network transactions take place in plaintext, it is possible for a hacker to "sniff" the data packets being transmitted and thus gain access to sensitive information. You can close this hole by using a secure shell utility like OpenSSH to create a secure encrypted "tunnel" for your data to pass through. Encrypting your connections in this manner makes it extremely hard for unauthorised users to read the data going back and forth between network hosts.
4. Disable unwanted services
Most Linux systems are installed with a wide variety of different services enabled, such as FTP, telnet, UUCP, ntalk and so on. In most cases, these services are rarely used and leaving them active is like leaving your windows open for a burglar to slip in. You can disable these services by commenting them out in the /etc/inetd.conf or /etc/xinetd.conf files and then restarting the inetd or xinetd daemon. Additionally, some services (for example, database servers) may start up by default during the boot process; you can disable these by editing the /etc/rc.d/* directory hierarchy. Many experienced administrators disable all system services, only leaving SSH communication ports open.
5. Use a spam and anti-virus filter
Junk e-mail and viruses annoy your users and can sometimes cause critical network failures. Linux is surprisingly resistant to viruses, but client machines running Windows may be more susceptible. Therefore, it's a good idea to install a spam and virus filter on your mail server itself, to "defang" suspicious messages and reduce the risk of a chain of collapses.
Begin by installing SpamAssassin, a leading open-source tool that uses a combination of different techniques to identify and flag spam; the program also supports user-based whitelisting and graylisting for greater accuracy. Next, install procmail for user-level filtering based on regular expressions; this tool allows automatic filtering of received email into mailboxes, at both a user and system level. Finally, install Clam Anti-Virus, a free anti-virus toolkit that integrates with sendmail and SpamAssassin and supports on-access scanning of email attachments.
6. Install an intrusion detection system
Intrusion detection systems (IDS) are early warning systems that let you know if changes occur on your network. They're a great way to identify (and prove) attempts to break into your system, although at the cost of increased resource consumption and potential red herrings. There are two fairly well-known IDS' you can try: tripwire, which tracks file signatures to detect modifications; and snort, which use rules-based directives to perform real-time packet analysis and search and identify attempts to probe or attack your system. Both packets can generate e-mail alerts (among other actions) and are useful when you suspect your network is being compromised but need definitive proof.
7. Perform regular security audits
When it comes to securing your network, this final step is possibly the most important. Here, you put on a black hat and do your best to circumvent the defences you erected in the previous steps. Doing this provides you with an immediate and objective assessment of how hard your system really is, and identifies potential vulnerabilities that you should fix.
A number of tools are available to help you in this audit: you can attempt to hack your password files using password crackers like Crack and John the Ripper; you can use nmap or netstat to look for open ports; you can sniff the network using tcpdump; and you can try exploiting publicised holes in your installed programs (Web server, firewall, Samba) to see if they offer a way in. If you do manage to find a way past your obstacles, rest assured that others will too; take immediate measures to close the openings.
Protecting your Linux system is an ongoing task, and so you shouldn't rest easy once you've done the steps above. Visit the Linux security forums for more security tips, and be proactive in monitoring and updating the security of your system. Good luck!
Subscribe to:
Posts (Atom)